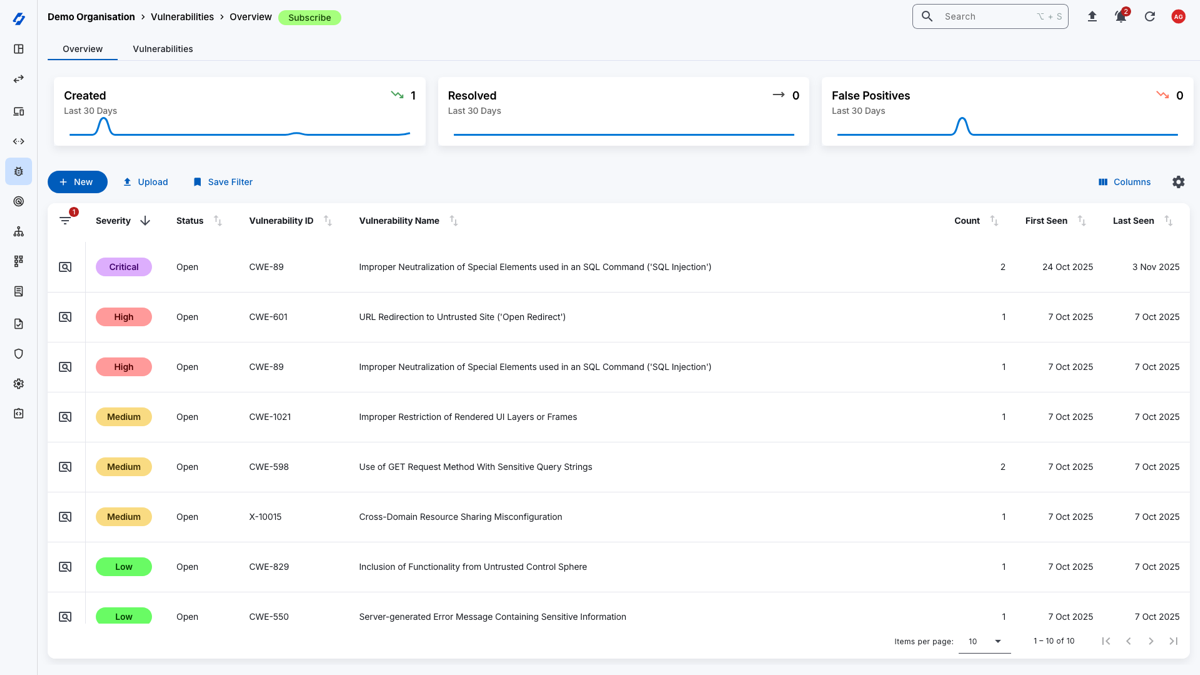
Automated Asset Discovery
Discover and Identify your Attack Surface – automatically
The Attack Surface Center provides seamless automated discovery of your attack surface without the complexity.
Automated Discovery runs unseen in the background to regularly identify assets and potential weaknesses within your attack surface.
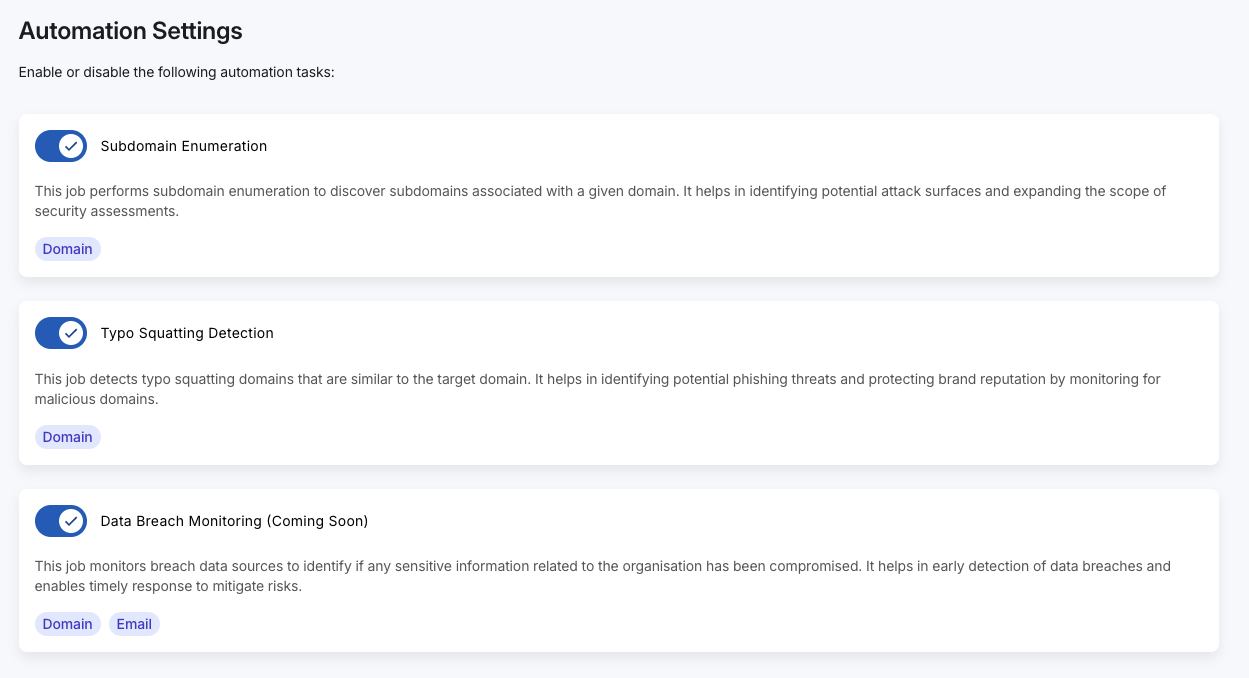
Discover Assets Unknown to You
Attack surface management is not only about maintaining your external perimeter – it’s about understanding what is exposed. The risks of shadow IT within cloud services has grown over the years, where resources and systems have been set up and long forgotten. This also counts for on-prem or colocation hosted infrastructure.
Subdomain Enumeration
Automatically scan your domains to identify subdomains you may not know existed.
- Dynamically updates your Attack Surface Map
- Runs automatically without the need for any configuration
- Creates and updates assets with the latest information discovered
We use a combination of subdomain enumeration techniques such as intelligence-led and curated lists to identify your potential subdomains, along with information gathered from Certificate Transparency logs to fingerprint your assets.
Typosquatting and Phishing Domains
One of the many attack vectors that a dedicated attacker may use is to mimic your domains through mis-typed or similar looking domain names. Our tools have you covered.
Our typosquatting and phishing domain tools will:
- Search for registered domains (and subdomains) that could be a risk to your organisation as a possible phishing endpoint.
- Include the discovery of homoglyph, hyphenated, and lookalike domains
Work collaboratively with your team, investigate the domains to assess any potential threat, and block the domains at the edge.
Once you’re subscribed and have verified your domain names the available automated discovery tools will regularly scan in the background without any scheduling or manual invocation required.
Yes – users with permission to manage automations have the ability to toggle the tools at any time.
No, the automated discovery tools will not interact with your resources, so there won’t be any traffic directed at your assets. If, in future, any additional tools are added to the Attack Surface Center that will directly interact with your assets these will be optional features that you can enable manually.
Yes – our team are busy working to integrate new features and toolsets to help you discover not only your external attack surface, but also your internal attack surface.
Sign up to the Attack Surface Center today for free and keep updated on our future releases!
Identify assets and potential threats without lifting a finger.
The Attack Surface Center is a powerful Attack Surface Management (ASM) platform that helps you discover, manage, and secure your attack surface.
With features like asset discovery, risk management, and vulnerability scanning, the Attack Surface Center provides you with the tools you need to protect your organisation from cyber threats.