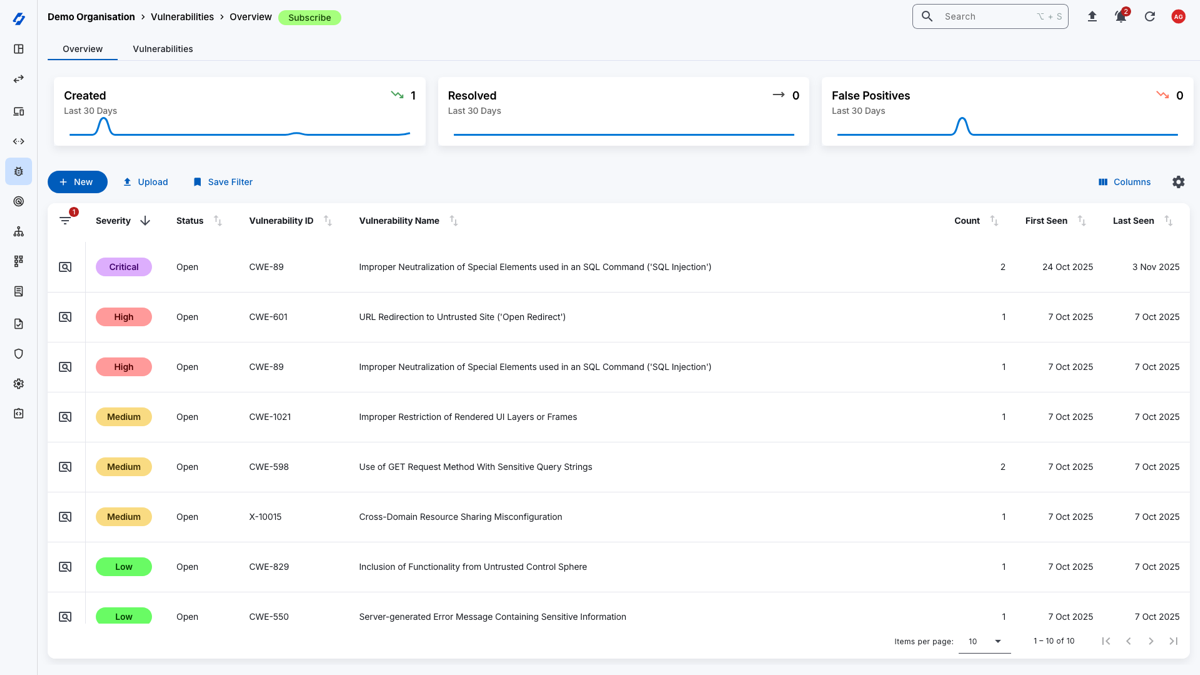
Vulnerability Scanning
Automate Your Vulnerability Scanning
Our platform provides an integrated solution for asset discovery, port scanning, and vulnerability scanning, allowing you to keep an eye on your attack surface.
With scheduled scanning, you can ensure that your assets are regularly scanned for vulnerabilities and exposed services, so you can easily track and manage vulnerabilities across your environment.
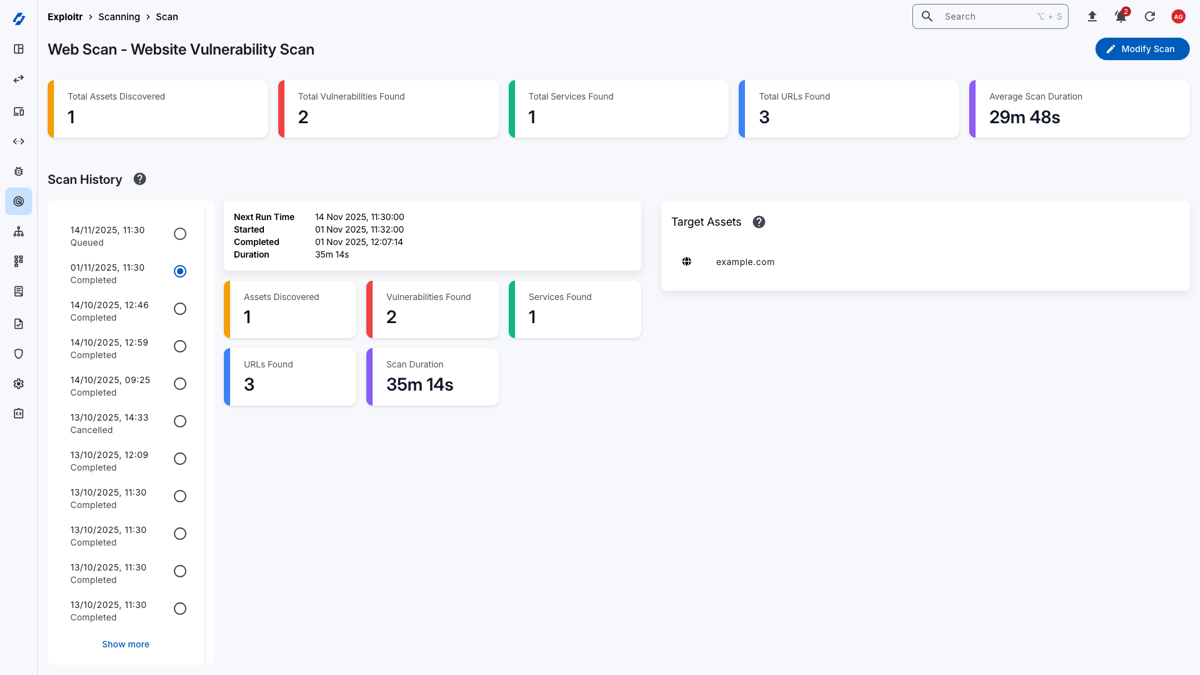
Network Port Scanning
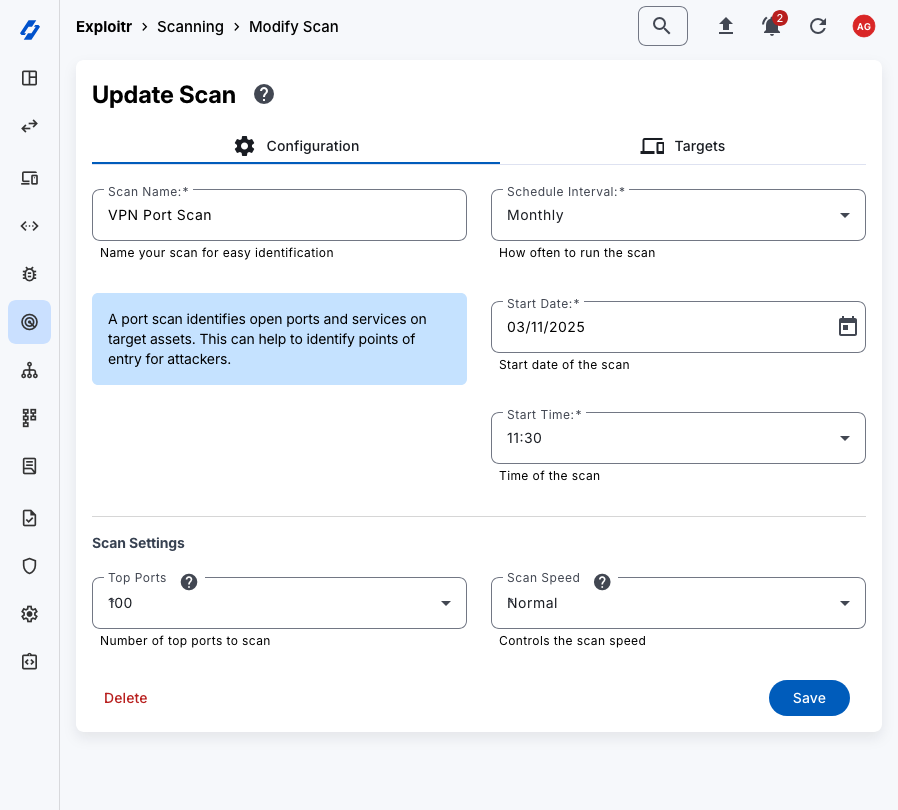
Create and manage port scanning jobs to discover open ports and services on your assets. This helps you identify potential attack vectors and understand the exposure of your assets.
- Create port scanning jobs for your assets
- Schedule scans to run at regular intervals as needed
- View scan results and identify open ports and services
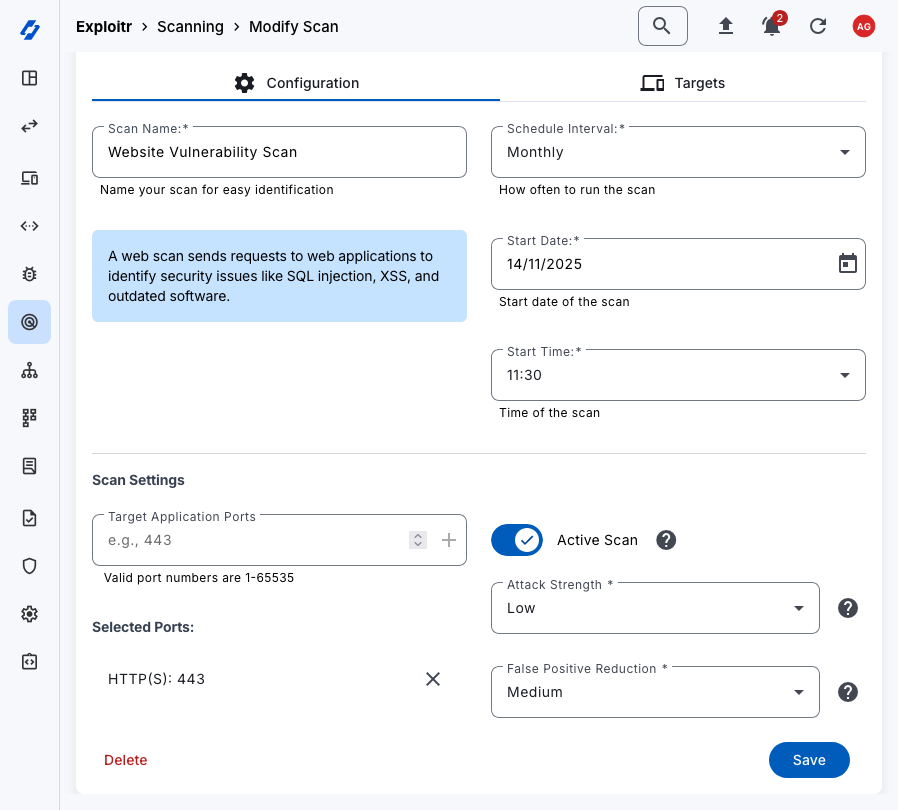
Web Application Vulnerability Scanning
Set up vulnerability scanning jobs to automatically scan your applications and APIs for known vulnerabilities. This helps you stay on top of your security posture and quickly address any issues.
- Create vulnerability scanning jobs for your assets
- Schedule scans to run at regular intervals as needed
- View scan results to remediate vulnerabilities in your applications and APIs
Automations
Utilise our automations to passively discover assets, services, and vulnerabilities in your environment without sending any traffic to your assets. This allows you to gather information about your assets without actively probing them.
Some of our automations include:
- Domain and subdomain discovery
- IP address enumeration
- Email address discovery and enumeration
- DNS enumeration
Get Started with Vulnerability Scanning
Sign up to the Attack Surface Center today and experience the benefits of automated vulnerability scanning and management to help map your attack surface.
How It Works
Our vulnerability scanning feature is designed to automate the process of identifying and managing vulnerabilities in your environment. Here’s how it works:
- Create Scanning Jobs: You can create port scanning and vulnerability scanning jobs for your assets. This involves selecting the assets you want to scan and configuring the scan settings.
- Schedule Scans: Once you’ve created a scanning job, you can schedule it to run at regular intervals, such as weekly, monthly, or annually. This ensures that your assets are regularly scanned for vulnerabilities and exposed services.
- View Scan Results: After a scan is completed, you can view the results in the Attack Surface Center dashboard. The results will show you any open ports, services, and vulnerabilities that were discovered during the scan.
- Remediate Vulnerabilities: With the scan results in hand, you can prioritise and remediate vulnerabilities based on their severity and impact on your organisation. The Attack Surface Center provides the tools to help you manage and track the remediation process.
- Continuous Monitoring: By scheduling regular scans, you can maintain an up-to-date view of your security posture and quickly address any new vulnerabilities that may arise.
The Attack Surface Center supports various types of vulnerability scans, including network port scanning and web application vulnerability scanning. You can create and manage scanning jobs to discover open ports, services, and known vulnerabilities in your applications and APIs.
You can schedule vulnerability scans to run at regular intervals that suit your needs by choosing from weekly, monthly, or annual schedules. This flexibility allows you to maintain an up-to-date view of your security posture.
Yes, if you exceed your monthly asset allowance, you can purchase additional assets at any time. This allows you to scale your scanning capabilities as your network grows or as you add new targets to monitor.
Port scanning focuses on discovering open ports and services on your assets, helping you identify potential attack vectors. Vulnerability scanning, on the other hand, involves scanning your applications and APIs for known vulnerabilities, allowing you to address security issues in your software.
Yes, the Attack Surface Center offers automations that allow you to passively discover assets, services, and vulnerabilities in your environment without sending any traffic to your assets. This helps you gather information about your assets without actively probing them.
Scan for vulnerabilities within your assets. Discover and remediate.
The Attack Surface Center is a powerful Attack Surface Management (ASM) platform that helps you discover, manage, and secure your attack surface.
With features like asset discovery, risk management, and vulnerability scanning, the Attack Surface Center provides you with the tools you need to protect your organisation from cyber threats.