Asset Management
Easily discover, monitor, and secure your Assets
Automatically discover, import, or manually create assets to build a centralised, actionable view of your organisation’s infrastructure with our Asset Management tool.

Build an accurate inventory of your assets
Asset management is a critical area of any security program. It involves the discovery, import, and manual creation of assets to build a centralised, actionable view of your organisation’s infrastructure. This process enhances decision-making across your security operations.
Create and Manage Assets
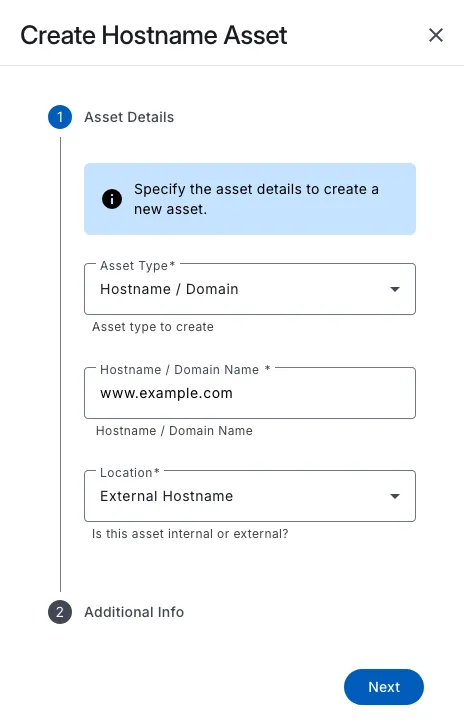
Easily create and manage assets with detailed information about each asset, its impact on your organisation, and assign them to groups for easier management.
You can easily select the type of asset you want to create, such as a hostname, domain, or IP address.

See Assets at a Glance
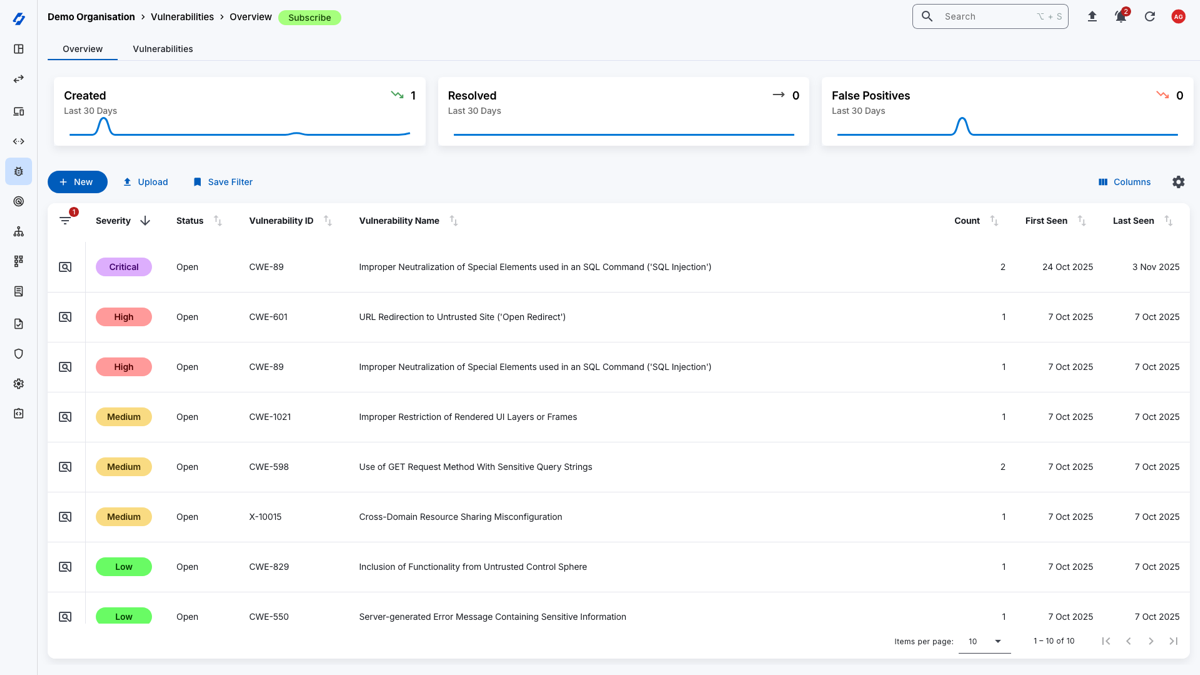
The Assets page provides a view of all assets across your organisation. You can filter and sort assets by various criteria, such as type, group, and risk score, to easily identify high-value assets and potential risks.
View individual asset details, including associated vulnerabilities, risk scores, and contextual information.
Quickly manage your organisational assets, understand the security posture of each asset and make informed decisions about remediation efforts.
Actionable Insights
Gain actionable insights into your security operations with the asset inventory, enabling you to track vulnerabilities and prioritise remediation efforts based on the criticality of each asset.
Easily identify high-value assets, track vulnerabilities associated with specific assets, and prioritise remediation efforts based on the criticality of each asset.


Services Overview
Easily view and manage services associated with your assets. The Services page provides an overview of all services, including open ports and protocols.
You can filter and sort services by various criteria, such as port number, protocol, and asset, to quickly identify potential attack vectors and understand the exposure of your assets.
Ready to take control of your asset management?
Sign up to the Attack Surface Center today and experience the benefits of streamlined asset management and enhanced security operations.
Automated Asset Discovery
Attack Surface Center provides automated asset discovery capabilities through DNS, WHOIS, and other sources, allowing you to quickly identify and import assets from various sources. This includes network devices, servers, applications, and cloud resources. By automating asset discovery, you can ensure that your asset inventory is always up-to-date and accurate.
This feature allows you to gather additional information about your assets without actively probing them, providing a more complete view of your infrastructure.
- Subdomain Discovery: Automatically discover subdomains associated with your assets, helping you identify potential attack surfaces.
- IP Address Enumeration: Gather information about IP addresses associated with your assets.
- Domain email enumeration: Identify email addresses associated with your domains, which can be useful for social engineering assessments.
- Email security checks: Perform security checks on domains to identify the presence of SPF, DKIM, and DMARC records, which can help prevent email spoofing and phishing attacks.
- DNS Enumeration: Automatically gather DNS records associated with your assets, including A, CNAME, MX, and TXT records.
- WHOIS Lookups: Retrieve WHOIS information for domains and IP addresses, including registration details and contact information.
- Certificate Transparency: Identify new assets through analysis of public certificate transparency logs, which can reveal newly issued SSL/TLS certificates associated with your domains.
Import Assets from External Sources
Consolidate asset information from multiple sources by importing assets from vulnerability scanners and other security tools. Our platform integrations also support AWS, GitHub, Cloudflare and other third-party services, allowing you to ingest assets directly from these platforms.
- Vulnerability Scanners: Import assets from popular vulnerability scanners.
- Custom Imports: Utilise our custom file format to import assets from any source, including spreadsheets and CSV files.
See what the Attack Surface Center can do for you
The Attack Surface Center is a powerful Attack Surface Management (ASM) platform that helps you discover, manage, and secure your attack surface.
With features like asset discovery, risk management, and vulnerability scanning, the Attack Surface Center provides you with the tools you need to protect your organisation from cyber threats.